Quantum computing has long been seen as a looming threat to the cryptographic foundations of blockchain technologies like Bitcoin and Ethereum. With headlines touting breakthroughs such as Google’s Willow chip (105 qubits as of December 2024) and IBM’s roadmap to thousands of qubits by 2029, many are wondering: can quantum computers crack Bitcoin’s security? And what about Ethereum? Let’s break it down with hard numbers and a clear look at the technology.
Bitcoin’s Cryptographic Armor: ECDSA and SHA-256
Bitcoin relies on two main cryptographic mechanisms:
- ECDSA (Elliptic Curve Digital Signature Algorithm): This secures Bitcoin’s private keys, ensuring only the rightful owner can sign transactions. It’s based on a 256-bit elliptic curve (secp256k1), making it a prime target for quantum attacks via Shor’s algorithm, which excels at solving discrete logarithm problems.
- SHA-256 (Secure Hash Algorithm): This hashing function underpins Bitcoin’s proof-of-work (PoW) mining and address generation. It’s a one-way function, meaning it’s computationally infeasible to reverse-engineer the input from the output—unless quantum computing changes the game.
Quantum computers threaten these systems differently. Shor’s algorithm could break ECDSA by deriving private keys from public keys, while Grover’s algorithm could weaken SHA-256 by speeding up the search for hash collisions or valid PoW nonces. But how many qubits would it take?
Qubits Needed to Crack Bitcoin
Breaking ECDSA (Bitcoin’s Signatures)
- Shor’s algorithm requires roughly 2n logical qubits to break an n-bit elliptic curve system (where n = 256 for Bitcoin’s secp256k1). That’s about 512 logical qubits at minimum.
- Accounting for error correction (quantum computers are noisy), estimates jump to 1,500–4,000 fault-tolerant qubits.
- A 2021 analysis from Imperial College London pegged it at ~1,500 qubits to derive a private key from a public key in a practical timeframe (e.g., 10 minutes, the Bitcoin block time).
Why this matters: If a quantum computer cracks ECDSA, it could steal funds from any address where the public key is exposed (e.g., after spending from a pay-to-public-key-hash address).
Breaking SHA-256 (Bitcoin’s Hashing)
- Grover’s algorithm offers a quadratic speedup, reducing the time to find a SHA-256 preimage or collision from 2^256 classical operations to 2^128 quantum operations.
- To crack SHA-256 in a day (e.g., to mine a block faster than the network or find a collision), researchers at the University of Sussex (2022) estimated 13 million qubits.
- For a 1-hour attack, it’s 317 million qubits, and for 10 minutes, it’s 1.9 billion qubits.
- A 2023 paper by Richard Preston suggested 2,593 error-corrected qubits could theoretically attack SHA-256, but real-world quantum gate overheads push practical estimates much higher.
Current State of Quantum Computing
As of February 2025:
- IBM’s most advanced quantum chip has 433 qubits (unerror-corrected), with plans for 4,000 by 2025.
- Google’s Willow chip has 105 qubits.
- We are still orders of magnitude away from the millions of fault-tolerant qubits needed—think decades, not years.
Is Bitcoin in Danger?
Not yet. Here’s why:
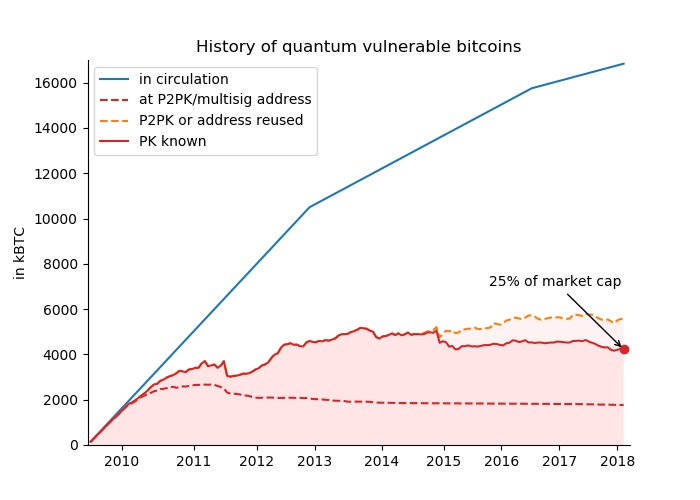
- ECDSA Risk: Only addresses with exposed public keys (e.g., pre-2010 coins or reused addresses) are vulnerable. A Deloitte study in 2022 found that 25% of Bitcoin (4 million BTC) could be at risk if quantum computers reach 1,500+ qubits. However, unspent, hashed addresses (pay-to-public-key-hash, or P2PKH) remain safe until funds are moved.
- SHA-256 Resilience: Breaking SHA-256 to disrupt mining or forge transactions requires millions of qubits—far beyond current technology. Even with Grover’s speedup, the energy and infrastructure costs would be astronomical, likely outpacing economic incentives.
- Adaptation: Bitcoin can fork to quantum-resistant algorithms (e.g., lattice-based cryptography) before the threat materializes. The community has time to prepare, given quantum progress is incremental and public.
What About Ethereum?
Ethereum shares Bitcoin’s reliance on ECDSA (256-bit) for signatures, so it faces similar quantum risks. A quantum computer with 1,500–4,000 qubits could derive private keys from public keys, threatening funds in exposed accounts. However, Ethereum’s hashing (Keccak-256, a SHA-3 variant) is structurally different from SHA-256 but still vulnerable to Grover’s algorithm, requiring millions of qubits to crack in a practical timeframe—similar to Bitcoin’s numbers.
Key Differences for Ethereum:
- Smart Contracts: Ethereum’s programmable nature means more public keys are exposed in contract interactions, potentially increasing vulnerability compared to Bitcoin’s simpler UTXO model.
- ETH 2.0 Backup: Ethereum’s roadmap includes plans for quantum resistance. Vitalik Buterin has proposed upgrades like ERC-4337 (account abstraction) and zero-knowledge STARKs to shield keys from quantum attacks, giving Ethereum a proactive edge.
- Faster Blocks: Ethereum’s 15-second block time (vs. Bitcoin’s 10 minutes) narrows the window for transit attacks, but the qubit threshold remains the same.
The Verdict
Quantum computing isn’t breaking Bitcoin or Ethereum anytime soon.
- Bitcoin’s ECDSA needs 1,500–4,000 qubits to crack, and SHA-256 demands 13 million to 1.9 billion qubits for a meaningful attack—numbers dwarfing today’s 433-qubit max.
- Ethereum faces the same ECDSA threat but benefits from faster adaptation potential.
- Both networks have years, if not decades, to transition to post-quantum cryptography as quantum technology matures.
The real danger isn’t the tech itself—it’s complacency.
If the crypto community ignores the slow march of quantum progress, a future with millions of qubits could expose vulnerabilities. But with active research into quantum-resistant algorithms (e.g., NIST’s post-quantum standards), Bitcoin and Ethereum can evolve faster than the threat.
For now, your BTC and ETH are safe from the quantum boogeyman.